Cybersecurity leaders and IT teams face heightened risks as the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has flagged a high-severity privilege escalation vulnerability in the Linux kernel. Identified as CVE-2023-0386 and carrying a CVSS score of 7.8, this flaw has been added to CISA's Known Exploited Vulnerabilities (KEV) catalog, underscoring the pressing need for immediate action.
Understanding the Threat: CVE-2023-0386
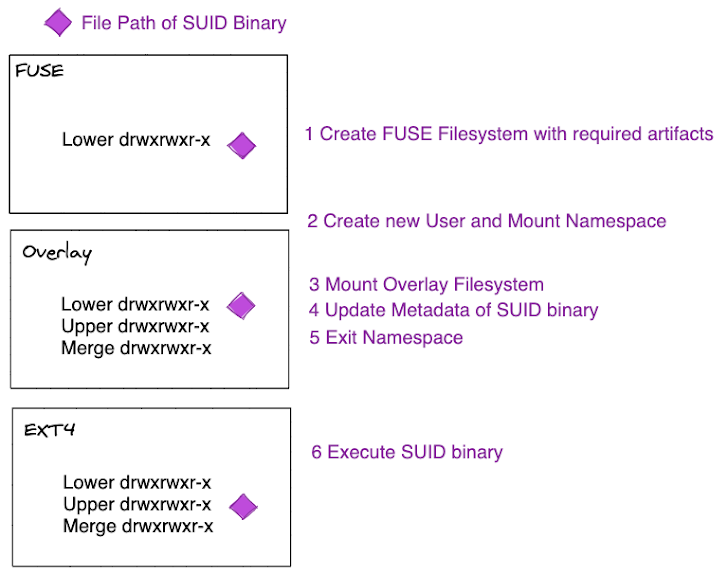
This vulnerability stems from improper ownership management in the Linux kernel's OverlayFS subsystem. Attackers can exploit a uid mapping bug that occurs when files with specific capabilities are copied from a 'nosuid' mount, enabling unauthorized execution of setuid files.
This loophole creates a pathway for local attackers to escalate privileges, potentially granting them root-level access.
Researchers at Datadog, who initially analyzed the issue, describe the exploit process as "trivial." Attackers can manipulate the kernel into generating a root-owned SUID binary in temporary directories, such as /tmp, and then execute it.
The flaw lies in how the kernel checks (or fails to check) ownership mappings within user namespaces during file copy operations.
Current Exploitation Landscape
Although CISA has not released detailed attack scenarios, the addition of CVE-2023-0386 to the KEV catalog signals that real-world exploitation is underway.
Security research has shown that attackers can move SUID binaries between directory layers using OverlayFS, effectively bypassing traditional security controls and making detection challenging.
- Security firm Wiz identified related vulnerabilities, dubbed GameOver(lay) (CVE-2023-32629, CVE-2023-2640), which facilitate similar privilege escalations.
- Federal Civilian Executive Branch (FCEB) agencies face a strict deadline to patch affected systems by July 8, 2025, as mandated by CISA, to prevent network compromises.
Wider Implications and Defensive Measures
The widespread adoption of Linux in critical infrastructure, cloud environments, and enterprise servers amplifies the potential impact of this vulnerability. Successful exploitation can lead to complete system takeover, lateral movement, and persistent threats across networks.
- Immediate patching is essential for all organizations, regardless of industry or scale, to block exploitation paths.
- Continuous monitoring of CISA's KEV catalog and proactive patch management are vital for defense against emerging threats.
- Experts recommend auditing OverlayFS configurations and restricting setuid binaries to minimize risk exposure.
CISA’s advisory highlights the ongoing danger of kernel-level vulnerabilities and the speed with which threat actors weaponize them. Swift remediation of CVE-2023-0386 and related flaws is crucial to safeguarding critical assets.
Effective cybersecurity demands both rapid response to known threats and a proactive stance to futureproof systems against evolving attack techniques.
Source: The Hacker News

CISA Issues Urgent Warning on Actively Exploited Linux Kernel Flaw